Google Indexing
Google started as a service but now became an essential part of our life, We all do all kinds of searching in google but ever thought what make us to ditch other search engines on comparison of Google
- Indexing
- What will be needed?
- finding FTP servers and websites using HTTPS
- Finding password logs
- Looking for configuration files with passwords
- How about mail?
Indexing
You may not have thought, but with the right approach to search, you can hack into accounts, devices, and simply find tons of sensitive infomation by simply entering querries into Google. Since Google does a great job of indexing everything related to the internet, it is possible to find files that were discovered by chance and contain infomation that is important to us.
What will be needed?
To do this, you will be need a browser with Internet access. Everything.
the grest thing about using Google dorks is that we can use tools available to almost everyone to find vulnerable systems.
“when your browser opens, go to google.com and we can get started.”
finding FTP servers and websites using HTTPS
First, we’ll use the following query to find file transfer servers published sometime in the past year.
Searching these servers may allow us to find should be internal but have unknowingly been made public.
intitle: "index of"
inurl: ftp after:2021
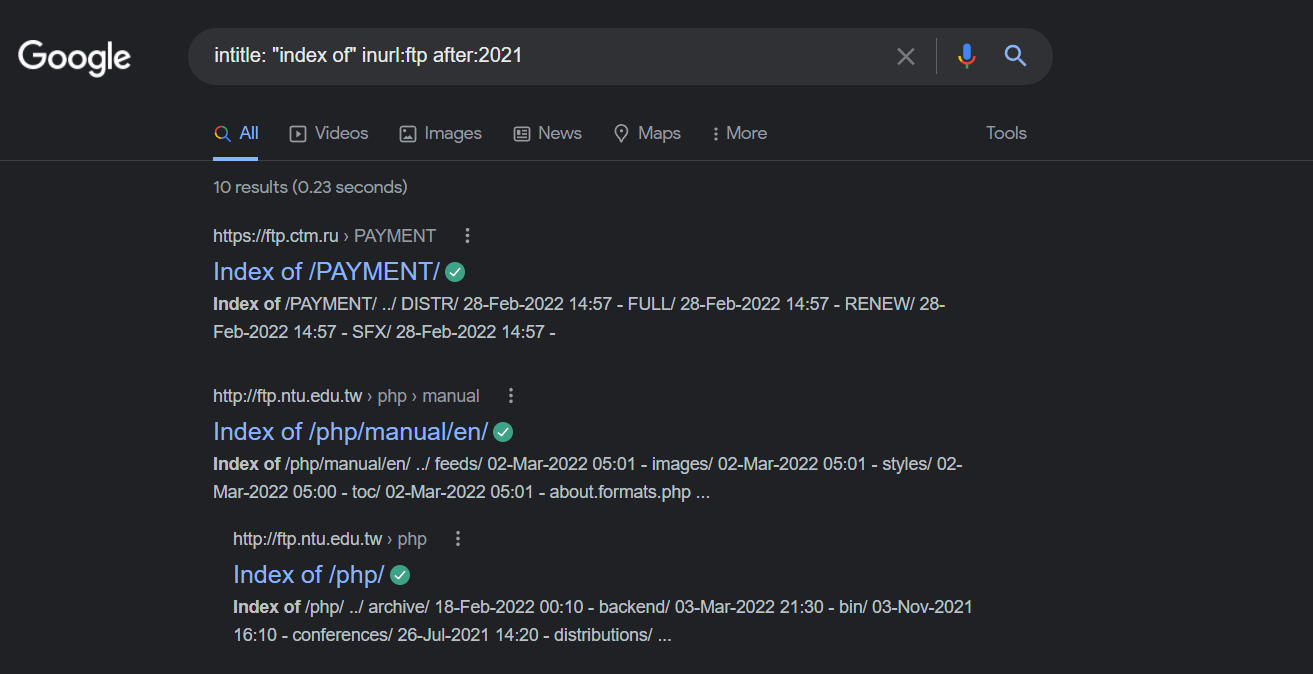
These servers are made public because their FTP server’s index file is data that google likes to crawl.
Google crawl results in a complete list of all files contained on the server.
If we want to find insecure webpages that are still using HTTPS for searching. We can modify the command slightly by chnanging “ftp” to “https” and re-executing the request.
intitle: "index of"
inurl: https after:2021
Searching this string should return a list of sites using HTTPS that are ready to be attacked. But if we’re looking for a specific type of site, we can go even further.
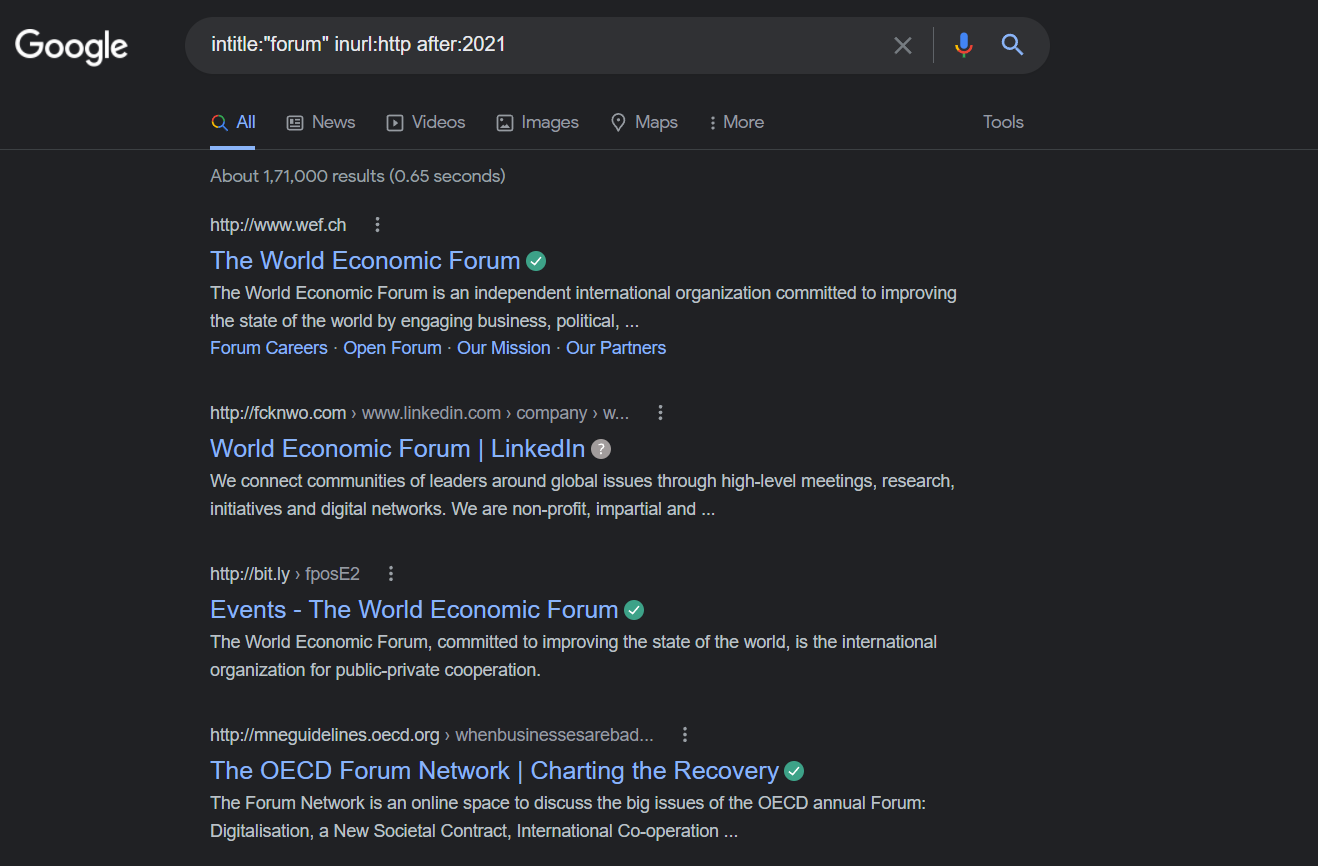
If we want to start attacking some simple targets, we can be more specific and search online forms while still using HTTPS by changing the text in the in the search header.
intitle: "forum"
inurl: https after:2021
We can keep adding search operators such as AND inurl: “registration” to get more specific information and look for insecure website registration pages.
Finding password logs
The next step is to search for .Log files.
Searching the LOG files will allow us to find out what credentials the system or different user or administrator accounts might have.
The trick we will use for this is the following.
allintext:password
filetype:log after:2021
When looking for current log files, we find this almost immediately.
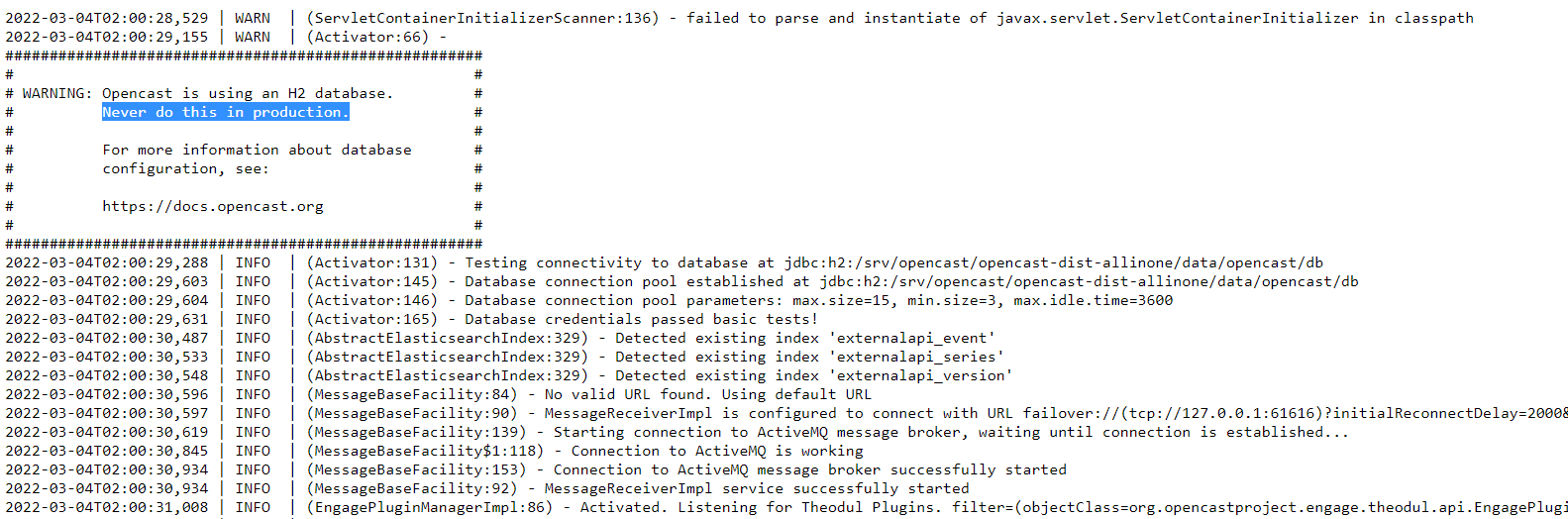
it indicates that the password has not changed and is still the same by default.
With a single request, we found the credentials of this sytem without hacking anything
Looking for configuration files with passwords
Configuration files should never be public and .ENV files are great example.
If we look for .ENV files that contain a string for a database password, we immediately find the password for that database that we discovered.
filetype:env "DB_PASSWORD" after:2021
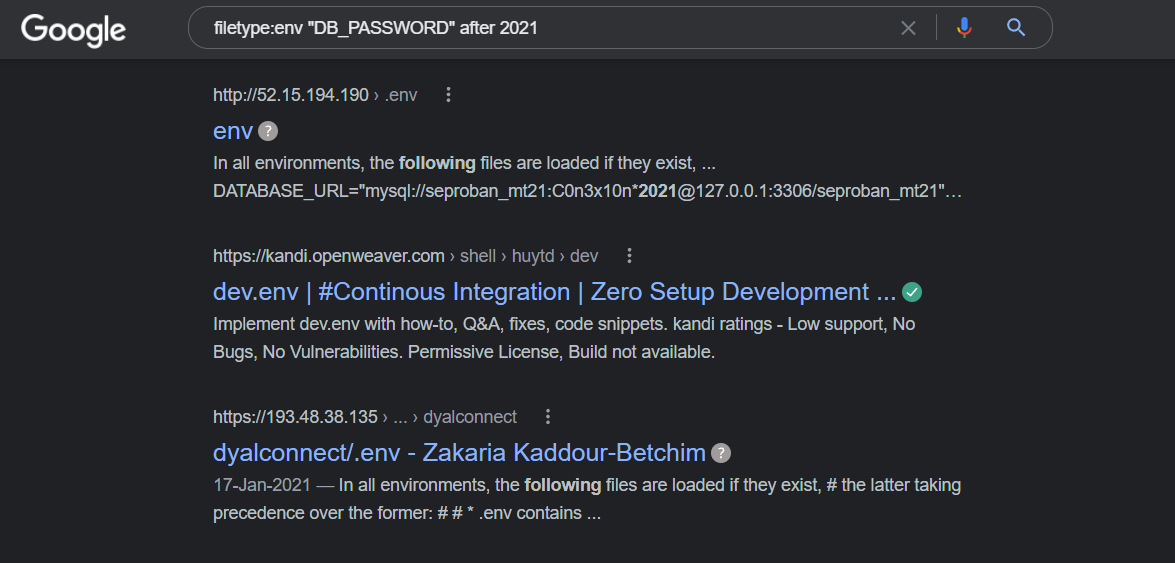
If we remove after:2018. we will see the old files, which also provide public access.
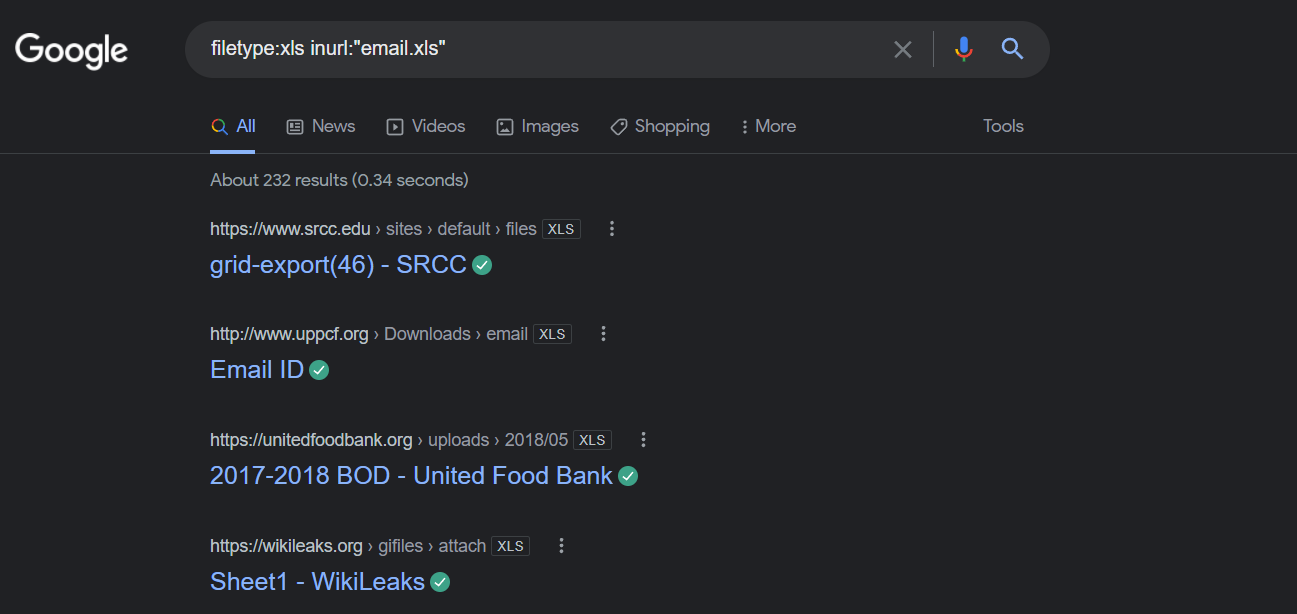
How about mail?
Email lists are a great way to sort things out and try to find information for corporate purpose.
These lists are often put up by companies, universities, or schools that are trying to put together email list for their people.
To find such mails, we will look for the speradsheet file types .XLS with the string email.xls in the URl.
Don’t open these files in your main OS. This could be the bait.
Don’t forget to give applause
PS: Applied in google for verification of this site, so first blog must have to be about google ;)
That’s all for 2day, c u 2morrow…
